Interconnectivity
Enable communication between all agents, break down data silos, and ensure AI has access to complete contextual information
Enabling All Agents to Connect and Communicate
Our vision is to
define how agents connect with each other,
building an open, secure, and efficient
collaboration network
for billions of intelligent agents.
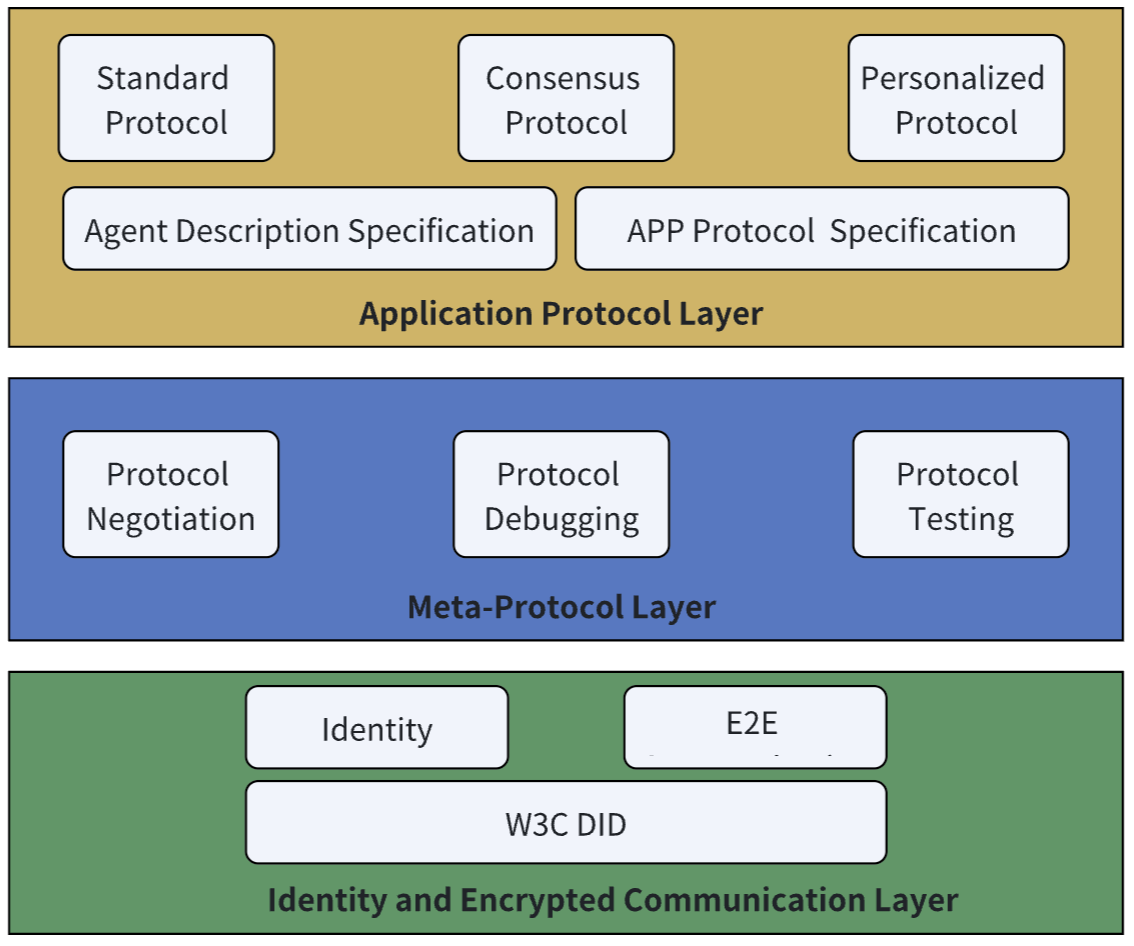
Decentralized authentication and end-to-end encrypted communication based on W3C DID standards.
Dynamic protocol negotiation enabling automatic-organizing agent networks.
Semantic-based capability description and efficient protocol management.